Integrating with Okta is a great way to provide the Single Sign-On experience to your Mediasite Users. Within this integration Okta is the Identity Provider (IdP) and Mediasite is Service Provider (SP).
Setting up SSO with Okta in Mediasite
1. Configure Okta Application
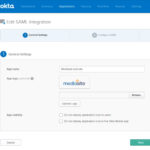
When configuring the Okta application, it is necessary to know which user attributes (e.g. First Name, Last Name, E-Mail, Roles) are being used in your organization and available to be sent to Mediasite (the Service Provider). This is configured in the Okta Admin Dashboard under Applications. Choose the Add Application button and then Create New App. Select a Web platform and SAML 2.0 as authentication type and click Create. This will start the Okta App Integration Wizard.
Okta App Integration Wizard.
| Field | Sample Value | Notes |
|---|---|---|
| App name | Mediasite | What you would like to call the Mediasite application within Okta. |
| App logo | https://(MEDIASITESERVER)/Mediasite/Lti/Client/mediasite_logo_72.png | Optional. Select any logo you would like to see within the Okta user interface for Mediasite. |
| App visibility | Unchecked | If you want to hide the Mediasite buttons from the end users Okta home page, then check these boxes. |
| Field | Sample Value | Notes |
|---|---|---|
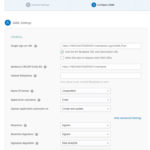
| Single sign on URL | https://(MEDIASITESERVER)/mediasite/Login/SAML/POST | e.g. http://mediasite.company.com/mediasite/login/SAML/POST. Typically, this is the URL of your server or some other unique name. |
| Audience URI (SP Entity ID) | https://(MEDIASITESERVER)/mediasite | e.g. http://mediasite.company.com/mediasite Typically, this is the URL of your server or some other unique name. |
| Default RelayState | blank | |
| Name ID format | Unspecified | |
| Application username | Email or other field you would like to use as the Username in Mediasite | If you change to a different field after integration, you will need to click the “Update Now” button to force all existing users to reset their usernames. |
| Update application username on | Create and update | |
| Response | Signed | |
| Assertion Signature | Signed | |
| Signature Algorithm | RSA-SHA256 | |
| Digest Algorithm | SHA256 | |
| Assertion Encryption | Unencrypted | |
| Enable Single Logout | Unchecked |
| Field | Sample Value | Notes |
|---|---|---|
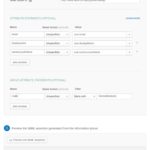
| Authentication context class | PasswordProtectedTransport | |
| Honor Force Authentication | Yes | |
| SAML Issuer ID | http://www.okta.com/$(org.externalKey) | |
| Attribute Statements | Email with Name format Unspecified and Value of user.email | You can add other items here. But we recommend at least including email, displayname. |
| Group Attributes Statements | Name roles with Name format Unspecified and Filter on the groups in Okta that you wish to send to Mediasite. | Optional, but can be useful to set Mediasite Roles for Security based on Group attributes in Okta. Note that filter of Matches regex .* will return all groups. |
| Feedback tab - Are you a customer or partner? | Select “I’m an Okta customer adding an internal app” |
Attribute Statements
It is recommended to release fields for “Email” that will usually return the “user.email” and DisplayName which will release “user.displayName” but that is configurable to your user contacts. “Roles” can also be released if you have a relevant field that includes information about the type of user this is. The role can be used to define permissions.
2. Configure Mediasite to Connect to Okta
Instructions:
- Browse to the Management Portal
- Click: Security > SAML 2.0 Configuration
- Complete the form using suggested values listed in the table below.
- Click: Save
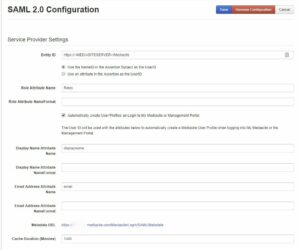
Service Provider Settings (AKA Mediasite)
| Field | Sample Value | Notes |
|---|---|---|
| Entity ID | https://mediasite_server_name/mediasite/ | e.g. http://mediasite.company.com/mediasite. Typically, this is the URL of your server or some other unique name. |
| Use the NameID in the Assertion Subject as the UserID | Checked | Use the NameID in the Assertion Subject as the UserID – If you do not want to release a separate attribute to uniquely identify a user, you can enable this option. This tells Mediasite to check the IdP assertion subject for the Name Identifier (NameID), and use that as the UserID instead. In most cases with Okta, you will use this option. Use an attribute in the Assertion as the UserID – This allows you to manually specify both the UserID attribute name and name format if selected. |
| UserID Attribute Name Format | If you have selected: Use an attribute in the Assertion as UserID, then leave this field blank. | |
| Role Attribute Name | Roles | Attribute used for retrieving security Roles from Okta. This is configured on the Okta application as Group Attribute Statements. In our example we will use the field name Roles |
| Role Attribute Name Format | This field should be left blank. | |
| Automatically create User Profiles on Login to My Mediasite or Management Portal | Enabled | This will automatically create new user Profiles for Management Portal and My Mediasite users. |
| Display Name Attribute Name | DisplayName | |
| Display Name Attribute Name Format | This field should be left blank. | |
| Email Address Attribute Name | ||
| Email Address Attribute Name Format | This field should be left blank. | |
| Metadata URL | N/A | Once valid SAML 2.0 Configuration settings have been saved, this URL should reflect the generated metadata. You will send this URL to your Okta administrator to use in step 1 above. |
| Cache Duration (Minutes) | 1440 | The length of time the SP will keep metadata and roles cached. The default is 1440 minutes (24 hours). |
Expiration Duration
| Field | Sample Value | Notes |
|---|---|---|
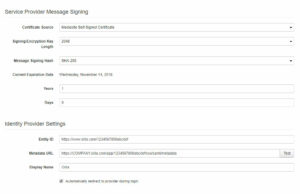
| Certificate Source | Mediasite Self-Signed Certificate | Use the self-signed certificate unless you have a requirement that a signed certificate is used. |
| Signing/Encryption Key Length | 2048 | |
| Message Signing Hash | SHA-256 | |
| Current Expiration Date | This displays the date when the current metadata is no longer valid and must be refreshed. This is automatically generated from the Expiration Duration setting. | |
| Expiration Duration | 1 Years, 0 Days | The time in years and days that the SP metadata will be valid. Save the Configuration Page so that the Current Expiration Date is populated. |
Identity Provider Settings
| Field | Sample Value | Notes |
|---|---|---|
| Entity ID | https://www.okta.com/(Okta_application_id) | Get this value from the Okta Administrator, or you can get it from the entityID field within the IdP’s metadata URL (See next row for details) This is the identifier of the IdP and must be globally unique. |
| Metadata URL | https://(Okta_site_name).okta.com/app/(okta_application_id)/sso/saml/metadata | e.g. https://company.okta.com/app/1234567890abcdefg/sso/saml/metadata |
| Display Name | Okta | Pick a friendly name that will display on the login page (e.g. Okta) |
| Automatically Redirect to provider during login | Checked | When checked, the user will be redirected to your Okta login page. When unchecked, all users will be directed to the standard Mediasite login form. This is useful for troubleshooting purposes. |
3. Update the Mediasite Login Form
After you have completed the SAML 2.0 Configuration form, you must update the Mediasite Video Platform to use the SAML based login form.
Self-Hosted Mediasite Video Platform
From within the Configuration Editor on the primary Web/Application server (e.g. http://localhost/mediasite/configure), update the login form to: https://<<MEDIASITE_SERVER>>/mediasite/login/SAML
Mediasite Cloud
Open a support case asking for the updates to be made.
4. Test
After Mediasite and Okta have been configured, you can begin testing the integration. To test the integration, perform the following steps:
- Open a new web browser
- Browse to the Mediasite Management Portal (e.g. http://mediasite.company.com/mediasite/manage).
- You will be redirected to your Okta login page. Enter your user credentials.
- The Mediasite Management Portal or My Mediasite portal should display.
- If you receive an error, the integration is not configured properly.
- If you have difficulty with embedding the SSO login page, check to see if Allow iFrame embedding is enabled in the general Okta settings. We recommend allowing this.